How UX monitoring can transform remote access technologies
Technologies that support remote access to IT desktops, servers and applications have become some of the most essential tools used by businesses, governments, schools, private individuals and countless others in 2020.
To maintain business continuity and strict social distancing mandates amid a global pandemic, digital workspaces and remote working models have become exceedingly common throughout the world. Even traditional businesses that have not embarked on large-scale IT initiatives have had to abruptly transform their ways of working.
Citrix Virtual Apps and Desktops, VMware Horizon, AWS Workspaces and AppStream, and Windows Virtual Desktops are just some of the technologies that enterprises are using to support remote employees and workers.
The abrupt changes that the pandemic has caused in workstyles has meant that most enterprises were not prepared. Some had not even thought of employees working remotely and connecting to their networks. Others had planned for a small portion of their employees working remotely—very few expected 100% of their workers to be remote.
As organisations started deploying and expanding their use of remote access technologies, user experience (UX) suffered, as many organisations were not adequately prepared to roll out virtualised applications and desktops.
Users complaining about slow logins, session disconnections, slow screen refreshes, and more have been common. As IT support teams also have had to be remote, the problems have been magnified.
An antidote for this problem has been much needed — because for remote employees to be productive, the technology they work with has to be reliable.
Conventional IT monitoring tools are not designed for virtualised applications and desktops. Also, these tools have often emphasised on monitoring server hardware and resources (CPU, memory, disk, etc.).
In the changed circumstances, with the focus on user experience, what organisations need is user experience (UX) monitoring. With proactive measurements of what a user is seeing, IT support teams can learn if their users are not productive, even before they get calls to the helpdesk from users.
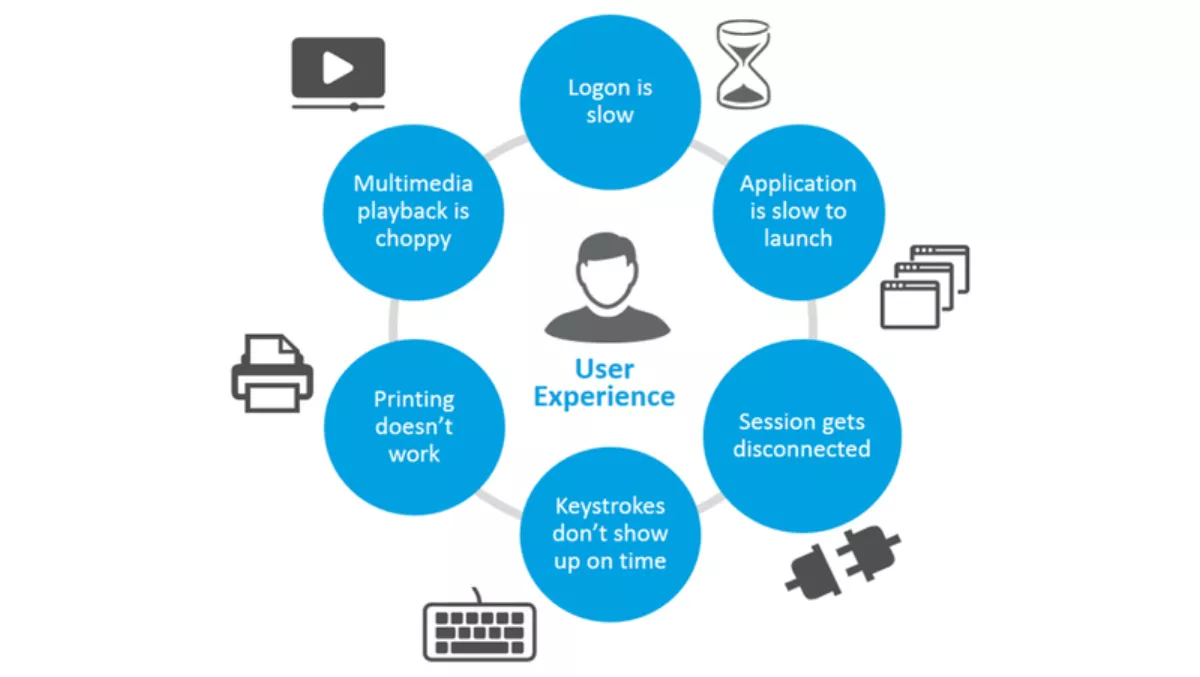
Knowing that there is an issue is one part of the problem, but then where is the root cause of the problem? Troubleshooting application slowness issues can often take several hours. With users connecting from wireless networks at home and with spotty internet connections, the problem could even be in their home network!
The UX monitoring solution
This is where eG Enterprise from eG Innovations comes in. Since 2003, eG Innovations has been working with remote access (or end-user computing technologies as they are sometimes called) of different kinds. According to the company, making UX central to the monitoring strategy is key to the success of digital workspace initiatives, and this is what eG Enterprise does.
The performance monitoring, diagnosis and reporting functions that eG Enterprise provides have become all the more critical with the broader usage of remote technologies and the need to ensure that users remain satisfied and productive.
So how can IT administrators benefit from eG Enterprise? eG Enterprise takes a four-step approach to UX monitoring.
Monitor all aspects of UX
Unlike web applications, there are many facets to a remote worker's user experience.
- What is their logon time?
- When they click on an application, how long does it take to launch and be responsive?
- When they use an application, how long does it take for a keystroke to show up?
- What is the bandwidth they are getting over the session (this is especially important if you are using collaboration tools like Microsoft Teams, Zoom etc.)?
If you proactively measure these facets of user experience, when a user calls, you will know if the problem is specific to that user, or whether it is affecting all the users. Even better, if you are keeping track of these measurements 24x7, you can even take action without waiting for user complaints.
eG Enterprise monitors real users' experience by passively observing user activity. At the same time, it also supports synthetic monitoring — where software robots deployed in different locations can test the services and report if there are any changes in performance or availability.
Being able to measure and report user experience is a crucial first step for UX monitoring. But when a user experience issue is detected (e.g., logon takes 90 seconds), IT administrators need to know what is causing the problem.
Monitor every layer and every tier supporting the digital workspace service
The digital workspace infrastructure supporting virtualised apps and desktops can be complex. There will be several network and firewall tiers, load balancers, web frontend servers, hypervisors, storage devices and so on.
Then there are the virtual desktops and the client applications. Many of these IT tiers are specialised for digital workspaces.
IT infrastructure services like DNS, DHCP, and Active Directory are also involved in supporting user accesses. If there is a problem in any of these tiers, users will complain that their virtual desktop or virtual app is slow.
To enable IT administrators troubleshoot user complaints quickly, it is vital to provide them with visibility into the operation of each of these tiers. A UX monitoring tool for remote access has to be able to monitor every layer and every tier of the infrastructure supporting the digital workspace service.
Sometimes, the problem may lie outside the infrastructure and the servers you control. For instance, there may be poor connectivity from a user's home or a problem in the public cloud that the user is accessing. UX monitoring with eG Enterprise allows IT admins to monitor these external dependencies as well.
Correlate performance across the Digital Workspace Tiers and pinpoint the root cause of problems
Finding the cause of a problem by sifting through millions of metrics collected is like finding a needle in a haystack! Tools like eG Enterprise use AI and machine learning to analyse metrics and determine where the cause of a problem lies and where the effects are.
Colour coded topology maps are then displayed so IT admins can easily determine what steps they have to take to remediate a problem. The ROI often lies in making the user interface simple to use, so even a helpdesk engineer can determine the troubleshooting path by looking at the dashboard. This frees up the time of expert IT admin staff so they can focus on more productive areas.
Get insights for optimisation, right-sizing and capacity planning
UX monitoring is not just about troubleshooting. eG Enterprise analyses the millions of metrics that are collected and provides insights and analytics that help admins to make informed decisions. They can perform a 'what if' analysis and determine how many more servers they need to support additional remote users.
They can also get recommendations on where and in what quantity additional resources need to be added, as well as the resulting additional capacity. Using these capabilities, your IT operations team will become analytical, intelligent, and effective.
The bottom line
UX has undoubtedly become more fundamental than ever before to a digital workspace in 2020, with the stakes becoming steadily higher. If the user experience is poor, in the best case, efficiencies and productivity will drop, users will complain, help desk tickets will increase, and the IT team will scramble to solve problems in response.
In the worst case, users will want IT to roll back the new technologies they have introduced – be it virtual desktops, cloud computing, or virtual storage – to regain the performance levels they are used to and rely on to do their jobs.
It's therefore essential to consider how UX can be improved. This was highlighted in a recent Gartner survey of enterprise customers, whereby 49% of respondents indicated that they had adopted Application Performance Management (APM) solutions to improve the quality of the customer/user experience. And, among the critical dimensions of APM, end-user experience monitoring was rated number one.
In the new normal, UX monitoring should be an integral part of any digital workspace deployment.
To learn more about eG Enterprise, click here.


